Azure Platform and Network Infrastructure Security fundamentals
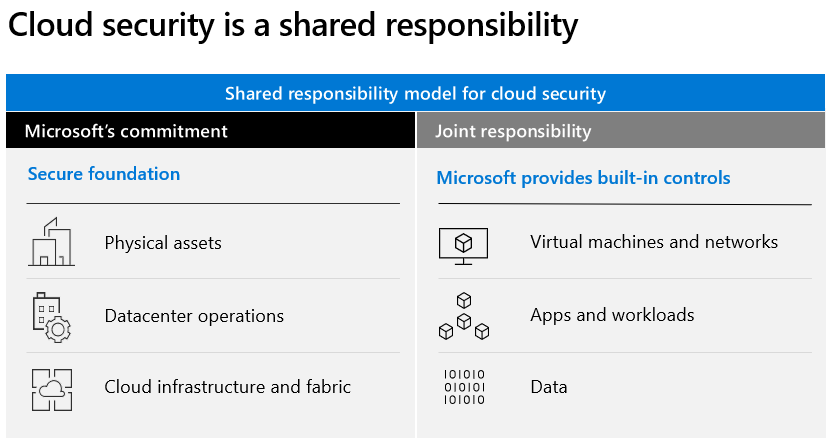
Microsoft Azure public cloud services support the same technologies millions of developers and IT professionals already rely on and trust. When we build on or migrate IT assets, public cloud service providers are relying on that organization’s abilities to protect applications and data with the services and the controls they provide to manage the security of cloud-based assets. We all know that security is job one in the cloud and how important it is that you find accurate and timely information about Azure security. One of the best reasons to use Azure for your applications and services is to take advantage of its wide array of security tools and capabilities. These tools and capabilities help make it possible to create secure solutions on the secure Azure platform. Microsoft Azure provides confidentiality, integrity, and availability of customer data, while also enabling transparent accountability. Overall cloud security is a shared responsibility. There’s stuff that Azure does and there’s stuff we do, and Azure Security Center helps us to figure out what the stuff we need to do:
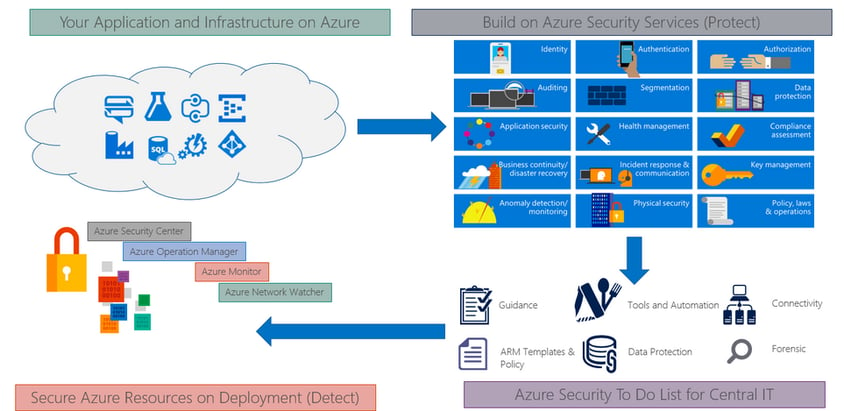
 Furthermore, Microsoft Azure is the only cloud computing provider that offers a secure, consistent application platform and infrastructure-as-a-service for teams to work within their different cloud skillsets and levels of project complexity, with integrated data services and analytics that uncover intelligence from data wherever it exists, across both Microsoft and non-Microsoft platforms as well as open frameworks and tools, providing choice for integrating cloud with on-premises and deploying Azure cloud services within on-premises datacenters. As part of the Microsoft Trusted Cloud, customers rely on Azure for industry-leading security, reliability, compliance, privacy, and the vast network of people, partners, and processes to support organizations in the cloud. Microsoft Azure provides services that help us meet security, privacy, and compliance needs. The following picture helps explain various Azure services available for us to build a secure and compliant application infrastructure based on industry standards.
Furthermore, Microsoft Azure is the only cloud computing provider that offers a secure, consistent application platform and infrastructure-as-a-service for teams to work within their different cloud skillsets and levels of project complexity, with integrated data services and analytics that uncover intelligence from data wherever it exists, across both Microsoft and non-Microsoft platforms as well as open frameworks and tools, providing choice for integrating cloud with on-premises and deploying Azure cloud services within on-premises datacenters. As part of the Microsoft Trusted Cloud, customers rely on Azure for industry-leading security, reliability, compliance, privacy, and the vast network of people, partners, and processes to support organizations in the cloud. Microsoft Azure provides services that help us meet security, privacy, and compliance needs. The following picture helps explain various Azure services available for us to build a secure and compliant application infrastructure based on industry standards.
 Microsoft Azure runs in datacenters managed and operated by Microsoft. These geographically-dispersed datacenters comply with key industry standards, such as ISO/IEC 27001:2013 and NIST SP 800-53, for security and reliability. The datacenters are managed, monitored, and administered by Microsoft operations staff. The operations staff has years of experience in delivering the world’s largest online services with 24 x 7 continuity.
Microsoft Azure runs in datacenters managed and operated by Microsoft. These geographically-dispersed datacenters comply with key industry standards, such as ISO/IEC 27001:2013 and NIST SP 800-53, for security and reliability. The datacenters are managed, monitored, and administered by Microsoft operations staff. The operations staff has years of experience in delivering the world’s largest online services with 24 x 7 continuity.
 Furthermore, Microsoft Azure is the only cloud computing provider that offers a secure, consistent application platform and infrastructure-as-a-service for teams to work within their different cloud skillsets and levels of project complexity, with integrated data services and analytics that uncover intelligence from data wherever it exists, across both Microsoft and non-Microsoft platforms as well as open frameworks and tools, providing choice for integrating cloud with on-premises and deploying Azure cloud services within on-premises datacenters. As part of the Microsoft Trusted Cloud, customers rely on Azure for industry-leading security, reliability, compliance, privacy, and the vast network of people, partners, and processes to support organizations in the cloud. Microsoft Azure provides services that help us meet security, privacy, and compliance needs. The following picture helps explain various Azure services available for us to build a secure and compliant application infrastructure based on industry standards.
Furthermore, Microsoft Azure is the only cloud computing provider that offers a secure, consistent application platform and infrastructure-as-a-service for teams to work within their different cloud skillsets and levels of project complexity, with integrated data services and analytics that uncover intelligence from data wherever it exists, across both Microsoft and non-Microsoft platforms as well as open frameworks and tools, providing choice for integrating cloud with on-premises and deploying Azure cloud services within on-premises datacenters. As part of the Microsoft Trusted Cloud, customers rely on Azure for industry-leading security, reliability, compliance, privacy, and the vast network of people, partners, and processes to support organizations in the cloud. Microsoft Azure provides services that help us meet security, privacy, and compliance needs. The following picture helps explain various Azure services available for us to build a secure and compliant application infrastructure based on industry standards.
 Microsoft Azure runs in datacenters managed and operated by Microsoft. These geographically-dispersed datacenters comply with key industry standards, such as ISO/IEC 27001:2013 and NIST SP 800-53, for security and reliability. The datacenters are managed, monitored, and administered by Microsoft operations staff. The operations staff has years of experience in delivering the world’s largest online services with 24 x 7 continuity.
Microsoft Azure runs in datacenters managed and operated by Microsoft. These geographically-dispersed datacenters comply with key industry standards, such as ISO/IEC 27001:2013 and NIST SP 800-53, for security and reliability. The datacenters are managed, monitored, and administered by Microsoft operations staff. The operations staff has years of experience in delivering the world’s largest online services with 24 x 7 continuity.
Physical network security
Azure is composed of a globally distributed datacenter infrastructure, supporting thousands of online services and spanning more than 100 highly secure facilities worldwide. The infrastructure is designed to bring applications closer to users around the world, preserving data residency, and offering comprehensive compliance and resiliency options for customers. Azure has 52 regions worldwide and is available in 140 countries/regions. Microsoft takes a layered approach to physical security, to reduce the risk of unauthorized users gaining physical access to data and datacenter resources. Datacenters managed by Microsoft have extensive layers of protection: access approval at the facility’s perimeter, at the building’s perimeter, inside the building, and on the datacenter floor. Layers of physical security are:- Access request and approval
- We 're required to provide a valid business justification for your visit; for example, compliance or auditing purposes.
- Facility’s perimeter
- When we arrive at a datacenter, we're required to go through a well-defined access point.
- Building entrance
- The datacenter entrance is staffed with professional security officers who have undergone rigorous training and background checks.
- Inside the building
- After we enter the building, we must pass two-factor authentication with biometrics to continue moving through the datacenter.
- Datacenter floor
- We are allowed only on the floor that we are approved to enter.
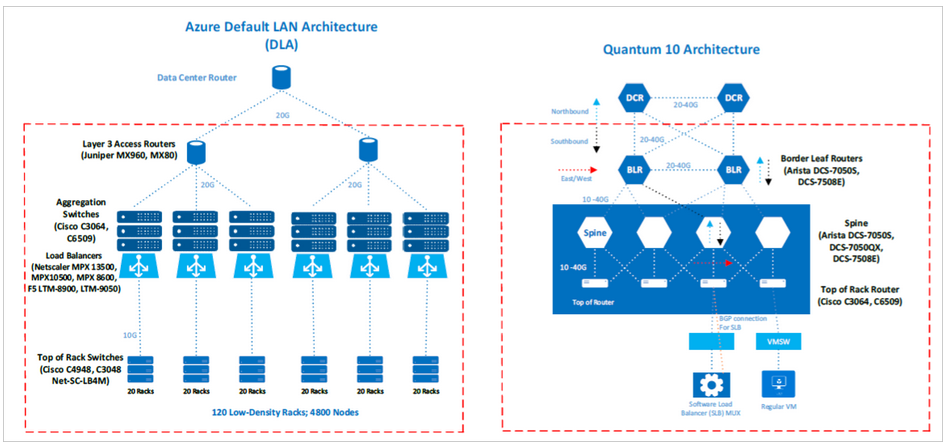
Azure network architecture
The Azure network architecture follows a modified version of the industry-standard core/distribution/access model, with distinct hardware layers. The layers include:- Core (datacenter routers)
- Distribution (access routers and L2 aggregation). The distribution layer separates L3 routing from L2 switching.
- Access (L2 host switches)
- Routers (datacenter, access router, and border leaf routers)
- Switches (aggregation and top-of-rack switches)
- Digi CMs
- Power distribution units

Azure production network
The users of the Azure production network include both external customers who access their own Azure applications and internal Azure support personnel who manage the production network. A globally redundant internal and external Azure Domain Name Service (DNS) infrastructure, combined with multiple primary and secondary DNS server clusters, provides fault tolerance. At the same time, additional Azure network security controls, such as NetScaler, are used to prevent distributed denial of service (DDoS) attacks and protect the integrity of Azure DNS services. Azure is hosted in geographically distributed Azure datacenters within the US, and it's built on state-of-the-art routing platforms that implement robust, scalable architectural standards. Among the notable features are:- Multiprotocol Label Switching (MPLS)-based traffic engineering, which provides efficient link utilization and graceful degradation of service if there is an outage.
- Networks are implemented with “need plus one” (N+1) redundancy architectures or better.
- Externally, datacenters are served by dedicated, high-bandwidth network circuits that redundantly connect properties with over 1,200 internet service providers globally at multiple peering points.
Management and operation of the Azure production network
The management and operation of the Azure production network is a coordinated effort between the operations teams of Azure and Azure SQL Database. The teams use several system and application performance-monitoring tools in the environment. And they use appropriate tools to monitor network devices, servers, services, and application processes. Focus for Operation Teams in azure are: Logging, Monitoring and Reporting- Primarily, the Microsoft Monitoring Agent (MMA) gathers monitoring and diagnostic log information from many places, including the fabric controller (FC) and the root operating system (OS), and writes it to log files.
- Azure Fabric platform offers distributed, multi-step deployment services, health monitoring, automatic repairs, and service version compliance. It provides the following services:
- Service modeling capabilities with high-fidelity development environment (datacenter clusters are expensive and scarce).
- One-click deployment and upgrade workflows for service bootstrap and maintenance.
- Health reporting with automated repair workflows to enable self-healing.
- Real-time monitoring, alerting, and debugging facilities across the nodes of a distributed system.
- Centralized collection of operational data and metrics for distributed root cause analysis and service insight.
- Operational tooling for deployment, change management, and monitoring.

