Introduction
We have recently had some issues accessing a few client servers and found it is related to a Windows security update that was released earlier in May 2018. The problem is when you try to RDP to a server you can receive an error similar to this:
An authentication error has occurred. The function requested is not supported Remote computer: <computer/hostname> This could be due to CredSSP encryption oracle remediation. For more information, see https://go.microsoft.com/fwlink/?linkid=866660
[caption id="attachment_104142" align="aligncenter" width="483"]
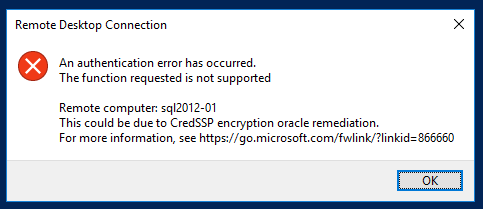 RDP error received[/caption] The error is the result of an update, Common Vulnerabilities and Exposures
CVE-2018-0886, being applied to the client machine and not the target servers (the client's production servers). This update will adjust the configuration of the credentials delegation on the system. It changes the configuration from
vulnerable to
mitigated which, if you are on a system that is set to a lower configuration, causes RDP access to be blocked.
RDP error received[/caption] The error is the result of an update, Common Vulnerabilities and Exposures
CVE-2018-0886, being applied to the client machine and not the target servers (the client's production servers). This update will adjust the configuration of the credentials delegation on the system. It changes the configuration from
vulnerable to
mitigated which, if you are on a system that is set to a lower configuration, causes RDP access to be blocked.
CVE details
This update applies to Windows 7 and up for desktop and Windows Server 2008 and higher. In Windows Server 2016 and 2012 R2, we found this update included in the May rollup update. The following are the two KB links for Windows 8.1 up to Windows Server 2016. If these get applied to your Windows 8.1 or Windows 10 desktop and not the servers, you will lose RDP access:
- KB4103723 - Windows 10 (1607), Windows Server 2016
- KB4103725 - Windows 8.1, Windows Server 2012 R2
Resolution
The end result is to apply the update to all of the target servers to ensure the security vulnerability is patched properly. If you utilize any management system for Windows Update (e.g. WSUS) you can push the update to the specific targets using that service. The update will require a reboot of the target server before it is applied. An interim approach is to set the Credential Delegation back to vulnerable on your workstation and this will open access back until you can apply the same patch to your servers.
Change credential delegation to vulnerable
You will need to do this logged in as a domain account that has elevated privileges on the workstation or server. Open a run prompt (Windows Key + R) and enter
gpedit.msc. Go to Computer Configuration > Administrative Templates > System > Credentials Delegation: [caption id="attachment_104143" align="aligncenter" width="298"]
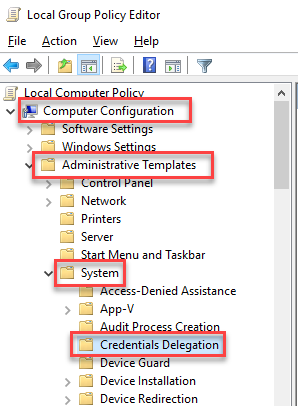 Credential Delegation policy[/caption] Open the setting "Encryption Oracle Remediation," then select "Enabled" and set the "Protection Level" to "Vulnerable": [caption id="attachment_104144" align="aligncenter" width="440"]
Credential Delegation policy[/caption] Open the setting "Encryption Oracle Remediation," then select "Enabled" and set the "Protection Level" to "Vulnerable": [caption id="attachment_104144" align="aligncenter" width="440"]
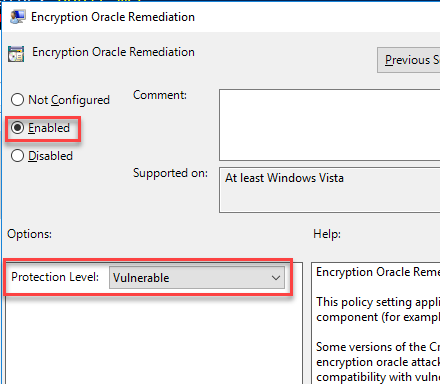 Protection Level to Vulnerable[/caption] Once you click OK you will then be able to RDP to the target servers again.
Protection Level to Vulnerable[/caption] Once you click OK you will then be able to RDP to the target servers again.
Add registry key
If you are not able to access Group Policy editor on the source/client machine you can simply add a registry key to perform the same task as above to temporarily regain access to your servers.
New-ItemProperty -Path 'HKLM:\Software\Microsoft\Windows\CurrentVersion' -Name AllowEncryptionOracle -Value 2 -PropertyType DWORD -Force
Post patch deployment
Once you have pushed the patch out to the servers you will need to "unconfigure" the Group Policy. Simply go back into that setting and select "Not Configured" and click OK. You will then regain access to all the servers again. If you used the registry option you can remove the registry key created using the following command:
Remove-ItemProperty -Path 'HKLM:\Software\Microsoft\Windows\CurrentVersion' -Name AllowEncryptionOracle -Force
 RDP error received[/caption] The error is the result of an update, Common Vulnerabilities and Exposures
CVE-2018-0886, being applied to the client machine and not the target servers (the client's production servers). This update will adjust the configuration of the credentials delegation on the system. It changes the configuration from
vulnerable to
mitigated which, if you are on a system that is set to a lower configuration, causes RDP access to be blocked.
RDP error received[/caption] The error is the result of an update, Common Vulnerabilities and Exposures
CVE-2018-0886, being applied to the client machine and not the target servers (the client's production servers). This update will adjust the configuration of the credentials delegation on the system. It changes the configuration from
vulnerable to
mitigated which, if you are on a system that is set to a lower configuration, causes RDP access to be blocked.
 Credential Delegation policy[/caption] Open the setting "Encryption Oracle Remediation," then select "Enabled" and set the "Protection Level" to "Vulnerable": [caption id="attachment_104144" align="aligncenter" width="440"]
Credential Delegation policy[/caption] Open the setting "Encryption Oracle Remediation," then select "Enabled" and set the "Protection Level" to "Vulnerable": [caption id="attachment_104144" align="aligncenter" width="440"]
 Protection Level to Vulnerable[/caption] Once you click OK you will then be able to RDP to the target servers again.
Protection Level to Vulnerable[/caption] Once you click OK you will then be able to RDP to the target servers again.

